In December 2023, Sophos X-Ops acquired a report of a false optimistic detection on an executable signed by a sound Microsoft {Hardware} Writer Certificates. Nevertheless, the model data for the supposedly clear file regarded just a little suspicious.
Determine 1: Model data of the detected file. Word the typos ‘Copyrigth’ and ‘rigths’
The file’s metadata signifies that it’s a “Catalog Authentication Shopper Service” by “Catalog Thales ” – presumably an try and impersonate the respectable firm Thales Group. Nevertheless, after digging into each our inner information and stories on VirusTotal, we found that the file was beforehand bundled with a setup file for a product named LaiXi Android Display screen Mirroring, “a advertising software program…[that] can join tons of of cell phones and management them in batches, and automate duties like batch following, liking, and commenting.”
It’s price noting that whereas we are able to’t show the legitimacy of the LaiXi software program – the GitHub repository has no code as of this writing, however accommodates a hyperlink to what we assume is the developer’s web site – we’re assured that the file we investigated is a malicious backdoor.
This isn’t the primary time Sophos X-Ops has seen risk actors abusing the Microsoft Home windows {Hardware} Compatibility Program (WHCP). In December 2022, virtually precisely a 12 months earlier than conducting this analysis, we reported that attackers had deployed cryptographically-signed drivers in a failed try and disable Sophos endpoint safety merchandise. These drivers, variants of BURNTCIGAR/POORTRY (an EDR killer offered on prison boards and linked to ransomware gangs corresponding to LockBit and CUBA) have been signed with a respectable WHCP certificates. Nevertheless, apart from the abuse of WHCP, we didn’t observe any proof that the December 2023 backdoor is in any means linked to that earlier EDR killer.
Simply as we did in 2022, we instantly reported our findings to the Microsoft Safety Response Heart. After validating our discovery, the group at Microsoft has added the related recordsdata to its revocation record (up to date at the moment as a part of the standard Patch Tuesday cycle; see CVE-2024-26234).
Whereas writing this text, which relies on our impartial analysis into this backdoor in December 2023, we turned conscious that Stairwell had printed its personal article on this subject in January 2024, based mostly on data in a tweet by Johann Aydinbas (additionally in January 2024). Our analysis validates and expands on a few of these findings.
As famous above, the risk actor behind the malicious file managed to acquire a Microsoft Home windows {Hardware} Compatibility Writer signature from Microsoft, so we began our evaluation from there.
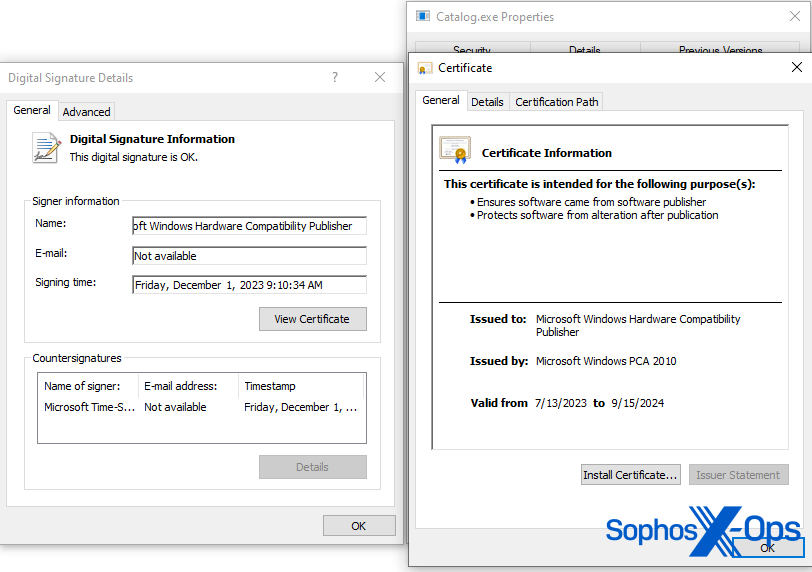
Determine 2: Signature of Catalog.exe
Authenticode is a Microsoft code-signing safety measure, which identifies the writer of an software and supplies verification that the appliance hasn’t been modified because it was signed and printed. Thankfully, Microsoft supplies code snippets on how one can course of these signatures and extract additional metadata from them. One of many items of data we have been capable of extract was the unique requesting writer.
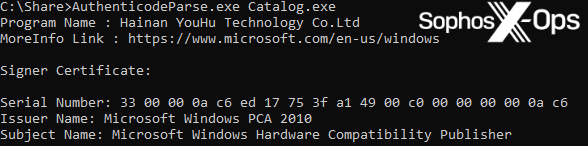
Determine 3: Extracting the unique requesting writer from the malicious file
On this case, the unique requesting writer is Hainan YouHu Expertise Co. Ltd, which can also be proven because the writer of the LaiXI software program.
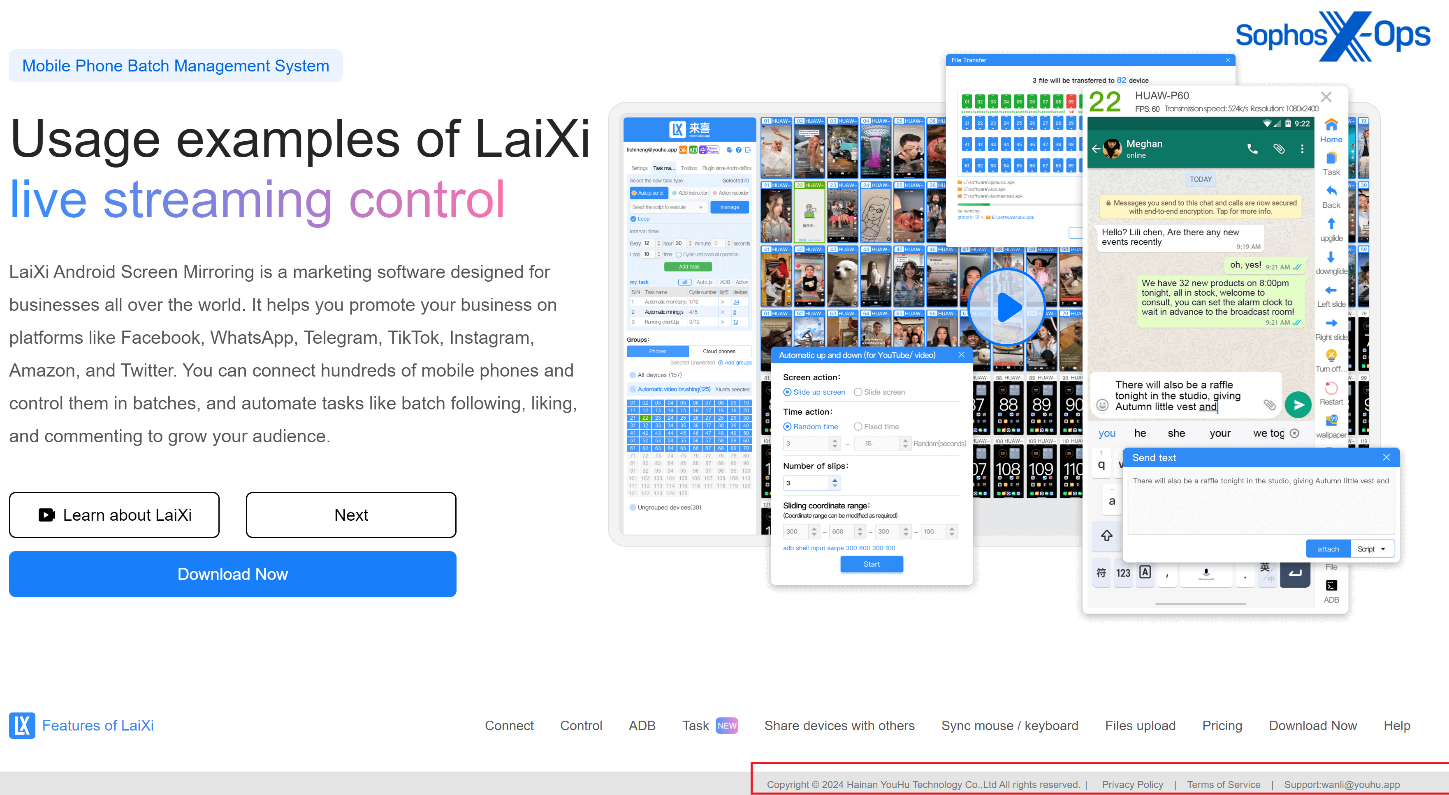
Determine 4: Hainan YouHu Expertise Co. Ltd can also be proven because the writer of the LaiXi software
We’ve got no proof to counsel that the LaiXi builders intentionally embedded the malicious file into their product, or {that a} risk actor carried out a provide chain assault to insert it into the compilation/constructing means of the LaiXi software. Nevertheless, we are going to be aware that given the hyperlinks between LaiXi and the malicious backdoor we investigated – and the size of time these hyperlinks have existed (since at the least January 2023, as we’ll talk about shortly) – customers ought to train excessive warning in terms of downloading, putting in, and utilizing LaiXi.
The suspicious file embeds a tiny freeware proxy server, known as 3proxy – a sketchy function for an authentication consumer. We assess that this embedded binary is meant to observe and intercept community visitors on an contaminated system.
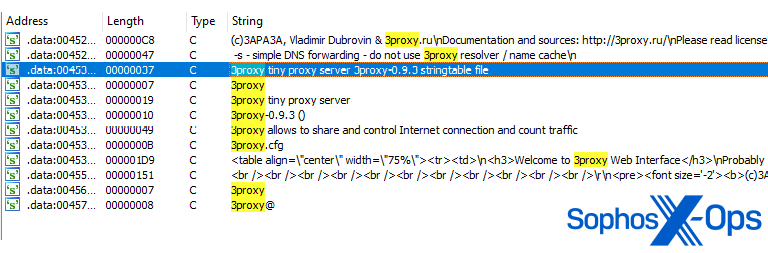
Determine 5: Strings referring to the embedded proxy server inside the malware
When the file executes, it installs itself as a service known as ‘CatalogWatcher’, with a service description of ‘Google ADB LoaclSocket [sic] Multi-threading Graphics API’ – an entire mismatch for the file model data proven in Determine 1. Whereas we are able to’t affirm it, we assess that that is linked to hyperlink to a setup file for the LaiXi Android software program, and an try and trick contaminated customers into believing that the service is respectable.
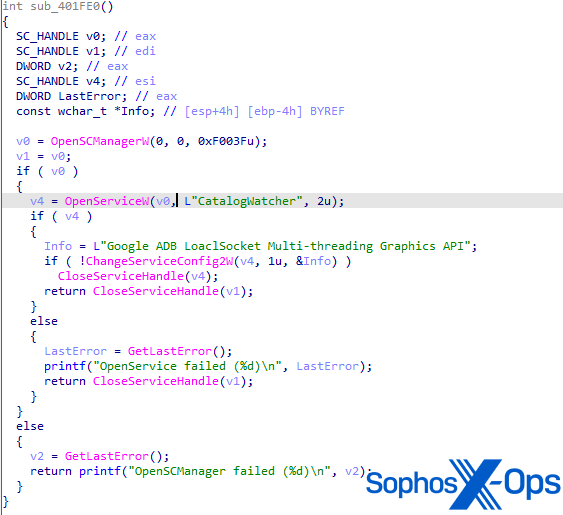
Determine 6: The perform for creating the CatalogWatcher service
As soon as the service runs, the malware queues a brand new work merchandise/thread through QueueUserWorkItem to the threadpool. As soon as the method has sufficient sources obtainable, the malicious thread begins. This thread embeds the core performance of the backdoor itself.
Curiously, this perform begins with an try and name the perform VmProtectBeginVirtualization(), which is an export of the VMProtectSDK32.DLL by VMProtect.
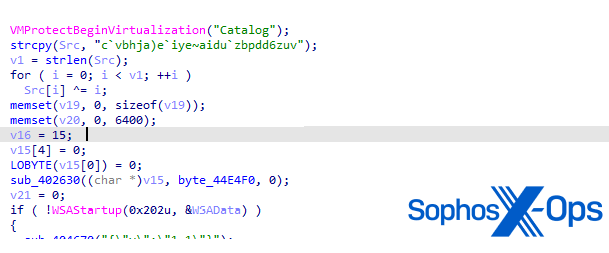
Determine 7: Begin of perform for C2 communication
As per the VMProtect person guide, this perform is used to outline areas of code to guard through obfuscation and virtualization. Official software program builders typically use digital machine-based code safety to assist forestall functions from being reverse-engineered – however risk actors additionally abuse it to try to thwart malware evaluation. For extra element on reverse-engineering functions that use digital machine-based safety, see a weblog I wrote on my private web site a number of years in the past. On this case, the perform shouldn’t be correctly obfuscated. We conclude that the risk actor might have supposed to do that, however failed for some unknown cause.
We additionally be aware that the POORTRY/BURNTCIGAR samples we reported to Microsoft in December 2022 have been filled with VMProtect. Again then, we already suspected that the attackers have been utilizing business packers corresponding to Armadillo or VMProtect to cover the software program’s malicious intent and get their drivers signed. It’s potential that the risk actor behind this backdoor was trying to do the identical (though we must always level out that the usage of obfuscation, packers, and virtualization – together with VMProtect – is quite common throughout many malware builders).
The C2 server string “catalog[.]micrisoftdrivers[.]com” – a lookalike area of microsoftdrivers[.]com – is decrypted through a easy XOR operation. A Python reimplementation of the decryption routine is under:
# Decrypts to catalog[.]micrisoftdrivers[.]com
s = “c`vbhja)e`iye~aidu`zbpdd6zuv”
cc = “”
i = 0
whereas i < len(s):
ch = chr((ord(s[i]) ^ i))
cc += ch
i += 1
Lastly, we needed to find out if the risk actor had embedded the identical payload into different merchandise. We checked each our personal telemetry and different sources, however noticed no proof that the backdoor has been bundled with something apart from LaiXi. We did, nonetheless, discover a number of different variants – a few of which have been linked to a file named ‘Laixi_Update_1.0.6.7_b.exe’, indicating that different recordsdata, not simply the setup installer, comprise the malicious backdoor.
We’ve categorized all of the samples we found into 4 teams, based mostly on the compilation timestamp.
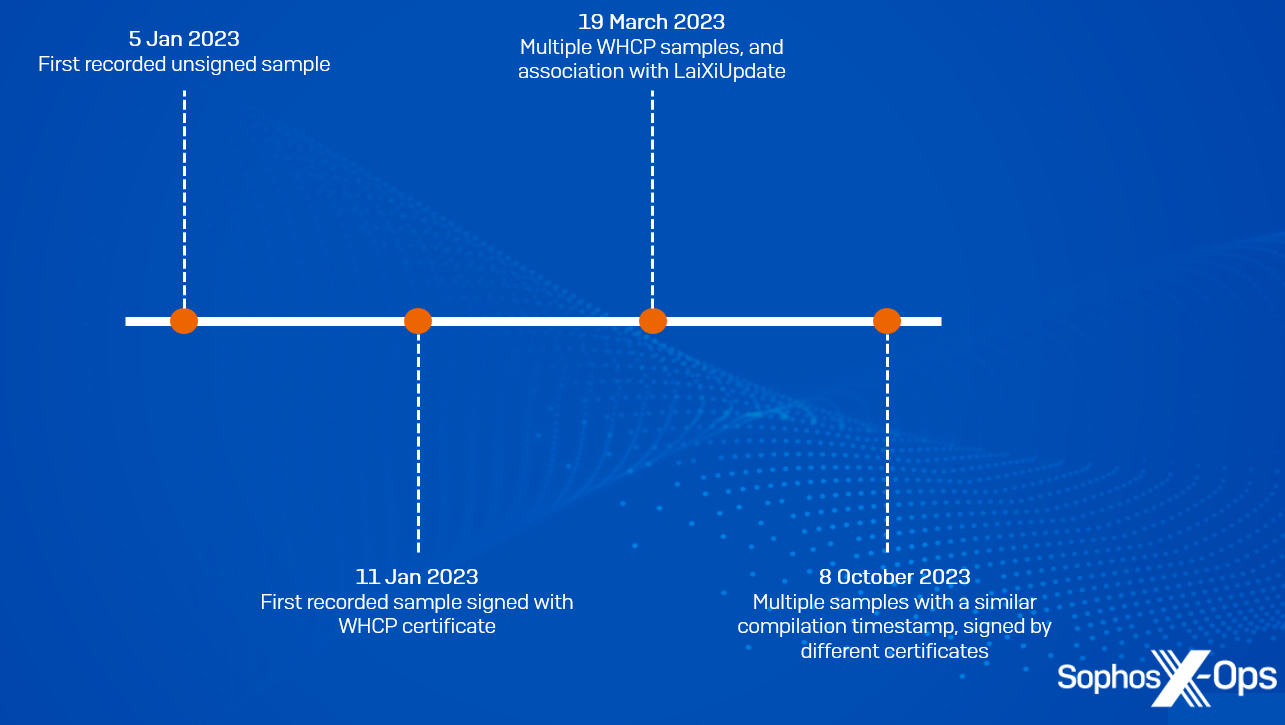
Determine 8: The 4 teams of samples and their chronological classifications
Whereas the compilation timestamp of a PE file may be faked, we regarded on the time delta between the second the file was compiled and the time it initially appeared in our programs, and assess that the compilation stamps are probably real.
The primary variant accommodates a compilation time of 2023-01-05. We subsequently assess that this marketing campaign has been in improvement since at the least January 2023
The second variant accommodates a compilation timestamp of 2023-01-11. That is additionally the primary pattern that managed to acquire a WHCP certificates
The third group of samples, with a compilation timestamp of 2023-03-19, have been both signed by the WHCP certificates, or unsigned. A few of these samples are related to the Laixi_Update_1.0.6.7_b.exe file talked about above
The ultimate group shares a compilation timestamp of 2023-10-08. Curiously, two samples of this group have been signed by a unique signer, though as of this writing we haven’t been capable of verify any additional data on these signers, or establish some other samples signed by them.
SHA256
Compilation Timestamp
Signature
cec73bddc33cd11ba515e39983e81569d9586abdaabbdd5955389735e826c3c7
2023-01-05 19:58:50
Not signed
815e21de6fab4b737c7dd844e584c1fc5505e6b180aecdd209fbd9b4ed14e4b2
2023-01-11 09:46:14
WHCP
3c931548b0b8cded10793e5517e0a06183b76fa47d2460d28935e28b012e426c
2023-03-19 14:19:29
WHCP
0dae9c759072f9c0e5a61a9de24a89e76da35ffab8ff9610cc90df417c741f3f
2023-03-19 14:19:34
WHCP
acc5c46ae2e509c59a952269622b4e6b5fa6cf9d03260bfebdfaa86c734ee6ea
2023-03-19 14:19:34
Not signed
230c9c47abb17e3caa37bcb1b8e49b30e671e6c50e88f334107e3350bee13385
2023-03-19 14:19:29
WHCP
d6a1db6d0570576e162bc1c1f9b4e262b92723dbabdde85b27f014a59bbff70c
2023-03-19 14:19:34
Not signed
4c23a199152db6596ccafb5ea2363500e2e1df04961a4ede05168999da87d39a
2023-10-08 17:05:40
Not signed
c0c648e98ec9d2576b275d55f22b8273a6d2549f117f83a0bcc940194f1d0773
2023-10-08 17:05:45
eccfd9f2d1d935f03d9fbdb4605281c7a8c23b3791dc33ae8d3c75e0b8fbaec6
2023-10-08 17:05:40
WHCP
5a519932c20519e58a004ddbfee6c0ed46f1cee8d7c04f362f3545335904bae2
2023-10-08 17:05:40
IFOX PTE. LTD
593f8ed9319fd4e936a36bc6d0f163b9d43220e61221801ad0af8b1db35a0de5
2023-10-08 17:05:40
Gaoyou tucker community studio
0ee12274d7138ecd0719f6cb3800a04a6667968c1be70918e31c6f75de7da1ba
2023-10-08 17:05:45
Not signed
Desk 1: A abstract of all of the samples we found, together with their compilation timestamp and signer
IoCs referring to this incident can be found on our GitHub repository. The Sophos safety Mal/Proxcat-A protects towards this malware and the variants we talk about right here.
Sophos X-Ops want to thank Richard Cohen, Andrew Ludgate (SophosLabs), and Sean Gallagher (Sophos X-Ops) for his or her assist in analyzing the samples; and Microsoft for participating with us to assist shield customers.





_dennizn_alamy_2.jpg?disable=upscale&width=1200&height=630&fit=crop&w=350&resize=350,250&ssl=1)














