The variety of gadgets contaminated with data-stealing malware in 2023 was 9.8 million, a sevenfold enhance over the identical determine for 2020, based on new analysis from Kaspersky Digital Footprint Intelligence. Nevertheless, the researchers imagine that the true determine might be as excessive as 16 million, as credentials from gadgets contaminated in 2023 will not be leaked onto the darkish internet till later this yr (Determine A).
Cybercriminals stole a mean of fifty.9 credentials per compromised system, and 443,000 web sites have had person data leaked prior to now 5 years.
The info was obtained from log recordsdata that report the actions of “infostealers.” Infostealers are a kind of malware that covertly extracts knowledge from contaminated gadgets with out encrypting it. These logfiles are “actively traded in underground markets” and monitored by Kaspersky as a part of its digital threat safety service.
Sergey Shcherbel, skilled at Kaspersky Digital Footprint Intelligence, mentioned in a press launch, “Leaked credentials carry a serious risk, enabling cybercriminals to execute numerous assaults comparable to unauthorized entry for theft, social engineering or impersonation.”
Why is the variety of data-stealing malware instances rising?
Infostealers are extra accessible
In accordance with a report by IBM, there was a 266% enhance in infostealing malware in 2023 over the earlier yr. It seems to be efficient, too, as incidences of criminals gaining entry by utilizing legitimate login credentials went up by 71%.
The recognition of infostealers is broadly regarded to be linked to the growing worth of company knowledge and the malware’s rising accessibility. In separate analysis, Kaspersky Digital Footprint Intelligence discovered that 24% of malware bought as a service between 2015 and 2022 was infostealers, which permit newbie cybercriminals to make the most of infostealers developed by one other group and distributed by way of the darkish internet.
Luke Stevenson, cyber safety product supervisor at managed service supplier Redcentric, informed TechRepublic in an electronic mail, “Stealer malware considerably lowers the entry barrier to would-be cyber criminals, making knowledge breaches simpler. Exfiltrated knowledge has fast worth regardless of the direct sufferer’s monetary assets and might be bought on shortly throughout the vary of illicit legal boards.
“The malware is comparatively simple to compile and deploy with supply codes accessible for these beginning out. Not like ransomware which has its personal enterprise ecosystem, these working infostealers usually have a lot decrease overhead prices.”
Aamil Karimi, risk intelligence chief at cybersecurity agency Optiv, informed TechRepublic in an electronic mail, “There was a notable rise in new stealer malware launched to the cybercriminal ecosystem starting in 2019, together with extremely popular strains like RedLine, Lumma and Raccoon. A few of these stealer malware variants have been utilized in ransomware operations which have proven elevated exercise over the previous few years. These variants are very cheap, and so they have confirmed to work, so there’s incentive for extra potential criminals to hitch these malware-as-a-service operations and affiliate applications.”
Moreover, the proliferation of “devoted leak websites,” the place stolen credentials are posted, gives extra targets for infostealers. The extra websites of this nature are energetic — and the quantity grew by 83%, based on Group-IB’s Hello-Tech Crime Developments 2022/2023 report — the upper the danger that firms may have their gadgets compromised. Analysis from Group-IB revealed the variety of firms that had their knowledge uploaded to leak websites in 2023 elevated by 74% over the earlier yr.
Provide chains have gotten extra advanced and susceptible
Another excuse that data-stealing malware instances are rising is as a result of provide chain. Third-party distributors are sometimes given entry to inner knowledge or use linked techniques and should present a better entry level that results in confidential knowledge belonging to the goal group.
Dr. Stuart Madnick, an IT professor and cybersecurity researcher on the Massachusetts Institute of Know-how, wrote within the Harvard Enterprise Evaluation, “Most firms have elevated the cyber safety of their ‘entrance doorways’ by means of measures comparable to firewalls, stronger passwords, multi-factor identification, and such. So, attackers search different — and generally extra harmful — methods to get it. Usually, which means coming in by way of distributors’ techniques.
“Most firms depend on distributors to help them, from doing air-con upkeep to offering software program, together with computerized updates to that software program. With a purpose to present these providers, these distributors want easy accessibility to your organization’s techniques — I refer to those because the ‘aspect doorways.’ However, these distributors are ceaselessly small firms with restricted cybersecurity assets.
“Attackers exploit vulnerabilities in these vendor techniques. As soon as they’ve some management over these vendor techniques, they’ll use the aspect door to get into the techniques of their prospects.”
Analysis from the Financial institution for Worldwide Settlements means that world provide chains have gotten longer and extra advanced, which will increase the variety of potential entry factors for attackers. A report from the Identification Theft Useful resource Heart discovered that the variety of organizations impacted by provide chain assaults surged by greater than 2,600 share factors between 2018 and 2023.
Malware sorts are growing in quantity
The quantity of malware out there to cybercriminals is growing exponentially, based on Optiv’s senior malware analyst McKade Ivancic, facilitating extra data-stealing assaults. He informed TechRepublic in an electronic mail, “The extra that stealer-family malware is authored, the extra these households’ code bases will likely be pilfered and re-written into comparable, but barely completely different, data-stealers.”
He added, “Safety groups, merchandise, signatures and the like can’t develop exponentially like malware can. Till a extra everlasting resolution is discovered, the ‘good guys’ will likely be naturally outpaced because of sheer numbers, compound progress, ease of entry, lack of enforcement and assault floor enlargement by way of rising expertise and software program investments.”
WFH and BYOD fashions are extra commonplace
Karimi informed TechRepublic, “The rise within the work-from-home and bring-your-own-device fashions since 2020 additionally probably contributed to elevated threat to firms whose workers’ gadgets weren’t centrally or responsibly managed.”
Private gadgets are likely to lack the identical safety measures as company-provided gadgets, creating a bigger assault floor for criminals trying to deploy data-stealing malware. Microsoft’s Digital Protection Report 2023 acknowledged that as much as 90% of ransomware assaults in 2023 originated from unmanaged or bring-your-own gadgets.
Should-read safety protection
What kind of credentials do cybercriminals goal?
The credentials usually focused by attackers utilizing data-stealing malware are those who might result in worthwhile knowledge, cash or privileged entry. Such particulars might embrace company logins for emails or inner techniques, in addition to social media, on-line banking or cryptocurrency wallets, based on the Kaspersky analysis.
SEE: Kaspersky’s Superior Persistent Threats Predictions for 2024
One other research by the agency discovered that over half (53%) of gadgets contaminated with data-stealing malware in 2023 have been company. This conclusion was drawn from the truth that the vast majority of contaminated gadgets with Home windows 10 software program are particularly operating Home windows 10 Enterprise (Determine B).
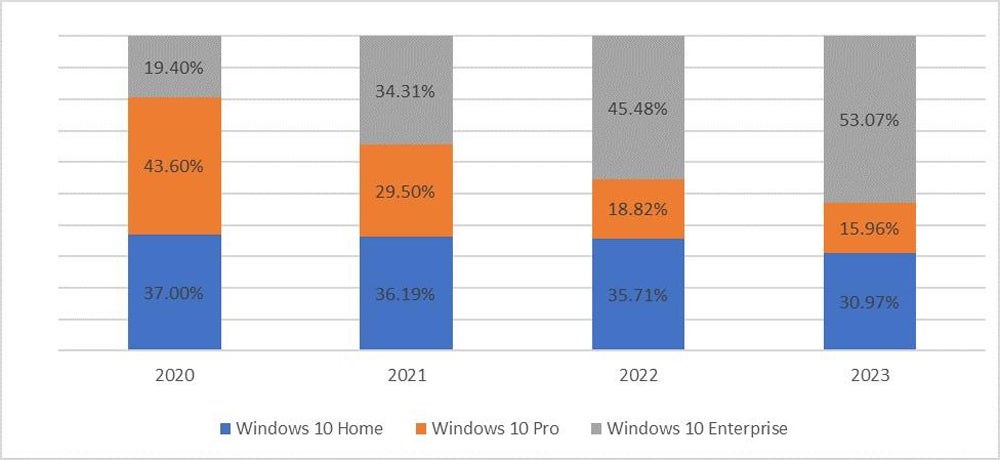
How a lot knowledge might be extracted with data-stealing malware?
Every log file analyzed by Kaspersky Digital Footprint Intelligence on this research contained account credentials for a mean of 1.85 company internet purposes, together with emails, inner portals and buyer knowledge processing techniques. Because of this criminals are sometimes capable of entry a number of accounts, each enterprise and private, after infecting a single system.
The log file knowledge additionally revealed {that a} fifth of workers would reopen the malware on their system greater than as soon as, giving the cybercriminals entry to their knowledge on a number of events with out the necessity for reinfection.
Shcherbel mentioned within the press launch, “This will point out a number of underlying points, together with inadequate worker consciousness, ineffective incident detection and response measures, a perception that altering the password is ample if the account has been compromised and a reluctance to analyze the incident.”
What do cybercriminals do with the stolen knowledge?
In accordance with Kaspersky Digital Footprint Intelligence, risk actors will use the credentials stolen from malware-infected gadgets for quite a lot of functions. These embrace:
Perpetrating cyberattacks on different events.
Promoting them to others on the darkish internet or shadow Telegram channels.
Leaking them without spending a dime to sabotage a company or higher their very own repute.
Shcherbel mentioned within the press launch, “The dark-web worth of log recordsdata with login credentials varies relying on the info’s attraction and the best way it’s bought there.
“Credentials could also be bought by means of a subscription service with common uploads, a so-called ‘aggregator’ for particular requests, or by way of a ‘store’ promoting not too long ago acquired login credentials solely to chose consumers. Costs sometimes start at $10 per log file in these outlets.
“This highlights how essential it’s each for people and corporations – particularly these dealing with giant on-line person communities – to remain alert.”
How can companies shield themselves from data-stealing malware?
To protect towards data-stealing malware, researchers at Kaspersky Digital Footprint Intelligence advisable the next:
Monitor darkish internet markets for compromised accounts related to the corporate.
Change the passwords of compromised accounts and monitor them for suspicious exercise.
Advise probably contaminated workers to run antivirus software program on all gadgets and take away any malware.
Set up safety options on firm gadgets that alert customers to risks like suspicious websites or phishing emails.
TechRepublic consulted different consultants for added recommendation.
Encryption and entry controls
Matthew Corwin, managing director at cybersecurity agency Guidepost Options, informed TechRepublic in an electronic mail: “Encryption of information each at relaxation and in transit is important for stopping data-stealing and publicity assaults, however for this to be efficient a complete defense-in-depth safety structure across the encrypted belongings can be required.”
Stevenson added that “securing accounts by way of password managers and multi-factor authentication” is a vital fundamental step for safeguarding account credentials from unauthorized use.
SEE: 6 Greatest Open-Supply Password Managers for Home windows in 2024
Threat assessments
Corwin informed TechRepublic, “Periodic safety and threat assessments may also help determine particular weaknesses in a company’s safety posture which might be exploited by risk actors utilizing data-stealing malware.”
Schooling
Karimi informed TechRepublic, “Creating a extra proactive method to threat administration requires schooling and consciousness — each for the IT workforce and safety directors, in addition to customers usually.
“Safety consciousness is commonly touted as a default advice, however threat consciousness shouldn’t be. It’s extra complete than a single on-line safety consciousness coaching module… It is very important set up processes to determine and observe essentially the most related threats which are distinctive to your setting.”
He added that “drafting, updating and implementing enterprise use instances and person insurance policies for internet exercise” can present further safety assurance by guaranteeing all employees are dealing with their credentials safely.





_dennizn_alamy_2.jpg?disable=upscale&width=1200&height=630&fit=crop&w=350&resize=350,250&ssl=1)














