A number of Apple prospects just lately reported being focused in elaborate phishing assaults that contain what seems to be a bug in Apple’s password reset characteristic. On this state of affairs, a goal’s Apple gadgets are compelled to show dozens of system-level prompts that stop the gadgets from getting used till the recipient responds “Enable” or “Don’t Enable” to every immediate. Assuming the consumer manages to not fat-finger the unsuitable button on the umpteenth password reset request, the scammers will then name the sufferer whereas spoofing Apple help within the caller ID, saying the consumer’s account is beneath assault and that Apple help must “confirm” a one-time code.
A few of the many notifications Patel says he obtained from Apple all of sudden.
Parth Patel is an entrepreneur who’s attempting to construct a startup within the conversational AI area. On March 23, Patel documented on Twitter/X a current phishing marketing campaign focusing on him that concerned what’s referred to as a “push bombing” or “MFA fatigue” assault, whereby the phishers abuse a characteristic or weak spot of a multi-factor authentication (MFA) system in a manner that inundates the goal’s gadget(s) with alerts to approve a password change or login.
“All of my gadgets began blowing up, my watch, laptop computer and telephone,” Patel advised KrebsOnSecurity. “It was like this method notification from Apple to approve [a reset of the account password], however I couldn’t do anything with my telephone. I needed to undergo and decline like 100-plus notifications.”
Some folks confronted with such a deluge might finally click on “Enable” to the incessant password reset prompts — simply to allow them to use their telephone once more. Others might inadvertently approve one among these prompts, which will even seem on a consumer’s Apple watch if they’ve one.
However the attackers on this marketing campaign had an ace up their sleeves: Patel mentioned after denying the entire password reset prompts from Apple, he obtained a name on his iPhone that mentioned it was from Apple Assist (the quantity displayed was 1-800-275-2273, Apple’s actual buyer help line).
“I choose up the telephone and I’m tremendous suspicious,” Patel recalled. “So I ask them if they will confirm some details about me, and after listening to some aggressive typing on his finish he offers me all this details about me and it’s completely correct.”
All of it, that’s, besides his actual title. Patel mentioned when he requested the pretend Apple help rep to validate the title they’d on file for the Apple account, the caller gave a reputation that was not his however fairly one which Patel has solely seen in background stories about him which might be on the market at a people-search web site referred to as PeopleDataLabs.
Patel mentioned he has labored pretty onerous to take away his info from a number of people-search web sites, and he discovered PeopleDataLabs uniquely and persistently listed this inaccurate title as an alias on his client profile.
“For some cause, PeopleDataLabs has three profiles that come up if you seek for my information, and two of them are mine however one is an elementary faculty trainer from the midwest,” Patel mentioned. “I requested them to confirm my title and so they mentioned Anthony.”
Patel mentioned the aim of the voice phishers is to set off an Apple ID reset code to be despatched to the consumer’s gadget, which is a textual content message that features a one-time password. If the consumer provides that one-time code, the attackers can then reset the password on the account and lock the consumer out. They will additionally then remotely wipe the entire consumer’s Apple gadgets.
THE PHONE NUMBER IS KEY
Chris is a cryptocurrency hedge fund proprietor who requested that solely his first title be used in order to not paint an even bigger goal on himself. Chris advised KrebsOnSecurity he skilled a remarkably related phishing try in late February.
“The primary alert I obtained I hit ‘Don’t Enable’, however then proper after that I obtained like 30 extra notifications in a row,” Chris mentioned. “I figured possibly I sat on my telephone bizarre, or was by accident pushing some button that was inflicting these, and so I simply denied all of them.”
Chris says the attackers continued hitting his gadgets with the reset notifications for a number of days after that, and at one level he obtained a name on his iPhone that mentioned it was from Apple help.
“I mentioned I’d name them again and hung up,” Chris mentioned, demonstrating the correct response to such unbidden solicitations. “Once I referred to as again to the actual Apple, they couldn’t say whether or not anybody had been in a help name with me simply then. They simply mentioned Apple states very clearly that it’s going to by no means provoke outbound calls to prospects — except the client requests to be contacted.”

Massively freaking out that somebody was attempting to hijack his digital life, Chris mentioned he modified his passwords after which went to an Apple retailer and acquired a brand new iPhone. From there, he created a brand new Apple iCloud account utilizing a model new e mail tackle.
Chris mentioned he then proceeded to get much more system alerts on his new iPhone and iCloud account — all of the whereas nonetheless sitting on the native Apple Genius Bar.
Chris advised KrebsOnSecurity his Genius Bar tech was mystified in regards to the supply of the alerts, however Chris mentioned he suspects that regardless of the phishers are abusing to quickly generate these Apple system alerts requires understanding the telephone quantity on file for the goal’s Apple account. In any case, that was the one side of Chris’s new iPhone and iCloud account that hadn’t modified.
WATCH OUT!
“Ken” is a safety business veteran who spoke on situation of anonymity. Ken mentioned he first started receiving these unsolicited system alerts on his Apple gadgets earlier this yr, however that he has not obtained any phony Apple help calls as others have reported.
“This just lately occurred to me in the midst of the evening at 12:30 a.m.,” Ken mentioned. “And despite the fact that I’ve my Apple watch set to stay quiet through the time I’m often sleeping at evening, it woke me up with one among these alerts. Thank god I didn’t press ‘Enable,’ which was the primary choice proven on my watch. I needed to scroll watch the wheel to see and press the ‘Don’t Enable’ button.”
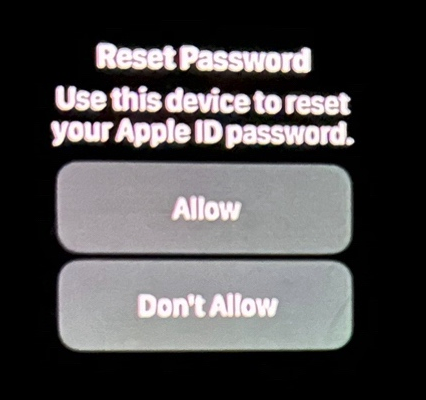
Ken shared this photograph he took of an alert on his watch that woke him up at 12:30 a.m. Ken mentioned he needed to scroll on the watch face to see the “Don’t Enable” button.
Ken didn’t comprehend it when all this was taking place (and it’s by no means apparent from the Apple prompts), however clicking “Enable” wouldn’t have allowed the attackers to vary Ken’s password. Somewhat, clicking “Enable” shows a six digit PIN that have to be entered on Ken’s gadget — permitting Ken to vary his password. It seems that these speedy password reset prompts are getting used to make a subsequent inbound telephone name spoofing Apple extra plausible.
Ken mentioned he contacted the actual Apple help and was finally escalated to a senior Apple engineer. The engineer assured Ken that turning on an Apple Restoration Key for his account would cease the notifications as soon as and for all.
A restoration secret is an non-obligatory safety characteristic that Apple says “helps enhance the safety of your Apple ID account.” It’s a randomly generated 28-character code, and if you allow a restoration key it’s alleged to disable Apple’s normal account restoration course of. The factor is, enabling it’s not a easy course of, and in the event you ever lose that code along with all your Apple gadgets you may be completely locked out.
Ken mentioned he enabled a restoration key for his account as instructed, however that it hasn’t stopped the unbidden system alerts from showing on all of his gadgets each few days.
KrebsOnSecurity examined Ken’s expertise, and may verify that enabling a restoration key does nothing to cease a password reset immediate from being despatched to related Apple gadgets. Visiting Apple’s “forgot password” web page — https://iforgot.apple.com — asks for an e mail tackle and for the customer to unravel a CAPTCHA.
After that, the web page will show the final two digits of the telephone quantity tied to the Apple account. Filling within the lacking digits and hitting submit on that kind will ship a system alert, whether or not or not the consumer has enabled an Apple Restoration Key.
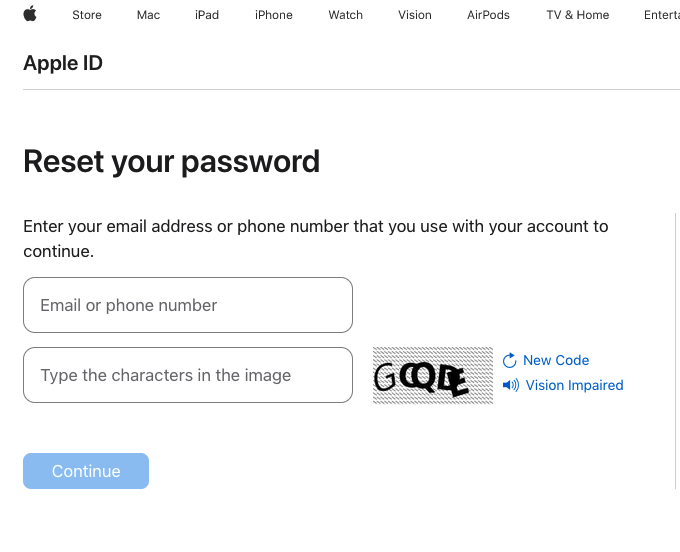
The password reset web page at iforgot.apple.com.
RATE LIMITS
What sanely designed authentication system would ship dozens of requests for a password change within the span of some moments, when the primary requests haven’t even been acted on by the consumer? May this be the results of a bug in Apple’s programs?
Apple has not but responded to requests for remark.
All through 2022, a prison hacking group referred to as LAPSUS$ used MFA bombing to nice impact in intrusions at Cisco, Microsoft and Uber. In response, Microsoft started imposing “MFA quantity matching,” a characteristic that shows a collection of numbers to a consumer trying to log in with their credentials. These numbers should then be entered into the account proprietor’s Microsoft authenticator app on their cellular gadget to confirm they’re logging into the account.
Kishan Bagaria is a hobbyist safety researcher and engineer who based the web site texts.com (now owned by Automattic), and he’s satisfied Apple has an issue on its finish. In August 2019, Bagaria reported to Apple a bug that allowed an exploit he dubbed “AirDoS” as a result of it might be used to let an attacker infinitely spam all close by iOS gadgets with a system-level immediate to share a file through AirDrop — a file-sharing functionality constructed into Apple merchandise.
Apple fastened that bug practically 4 months later in December 2019, thanking Bagaria within the related safety bulletin. Bagaria mentioned Apple’s repair was so as to add stricter price limiting on AirDrop requests, and he suspects that somebody has discovered a option to bypass Apple’s price restrict on what number of of those password reset requests could be despatched in a given timeframe.
“I feel this might be a legit Apple price restrict bug that ought to be reported,” Bagaria mentioned.
WHAT CAN YOU DO?
Apple appears requires a telephone quantity to be on file in your account, however after you’ve arrange the account it doesn’t need to be a cell phone quantity. KrebsOnSecurity’s testing exhibits Apple will settle for a VOIP quantity (like Google Voice). So, altering your account telephone quantity to a VOIP quantity that isn’t broadly identified can be one mitigation right here.
One caveat with the VOIP quantity concept: Except you embody an actual cellular quantity, Apple’s iMessage and Facetime purposes shall be disabled for that gadget. This would possibly a bonus for these involved about lowering the general assault floor of their Apple gadgets, since zero-click zero-days in these purposes have repeatedly been utilized by spy ware purveyors.
Additionally, it seems Apple’s password reset system will settle for and respect e mail aliases. Including a “+” character after the username portion of your e mail tackle — adopted by a notation particular to the positioning you’re signing up at — helps you to create an infinite variety of distinctive e mail addresses tied to the identical account.
As an illustration, if I have been signing up at instance.com, I’d give my e mail tackle as krebsonsecurity+instance@gmail.com. Then, I merely return to my inbox and create a corresponding folder referred to as “Instance,” together with a brand new filter that sends any e mail addressed to that alias to the Instance folder. On this case, nevertheless, maybe a much less apparent alias than “+apple” can be advisable.
Replace, March 27, 5:06 p.m. ET: Added perspective on Ken’s expertise. Additionally included a What Can You Do? part.





_dennizn_alamy_2.jpg?disable=upscale&width=1200&height=630&fit=crop&w=350&resize=350,250&ssl=1)














/cdn.vox-cdn.com/uploads/chorus_asset/file/25547838/YAKZA_3840_2160_A_Elogo.jpg?w=120&resize=120,86&ssl=1)