The primary Sophos Lively Adversary Report of 2024 presents what the Sophos X-Ops Incident Response (IR) crew has realized in regards to the present adversary panorama from tackling safety crises world wide. Our report is predicated on knowledge from over 150 circumstances drawn from the 2023 workload of the IR crew. We offer extra element on the demographics represented on this evaluation on the finish of the report.
As has been commonplace for Sophos’ Lively Adversary stories, this version incorporates knowledge from earlier years of IR casework, stretching again to the launch of our IR service in 2020. Whereas this report will primarily give attention to the evaluation of circumstances investigated by the IR crew throughout 2023, we may also take an extended view of the information, the place relevant, to grasp any significant modifications and developments — and, generally, the dearth thereof.
A second report, to be issued in late summer time, will incorporate knowledge from the primary half of 2024 – in different phrases, the circumstances we’re engaged on proper now, and circumstances which have but to happen. The everlasting battle between attackers and defenders has cycles, inflection factors, and currents all its personal. Protecting a detailed eye on these rhythms even when issues appear to be oh-so-quiet is vital for defenders seeking to perceive and react.
Key takeaways
Ransomware ranges have reached homeostasis
Timelines have stabilized
Tooling is stagnant
Zero days aren’t the actual downside
And nonetheless, defenses aren’t maintaining
The place the information comes from
For this report, the information for which as all the time is drawn from the circumstances tackled by our external-facing Incident Response crew, 88% of the dataset was derived from organizations with fewer than 1000 workers. As in earlier years, over half (55%) of organizations requiring our help have 250 workers or fewer. Twelve % of the organizations with which IR labored in 2023 have been firms with over 1000 workers, down from 19% in 2022. (For a glimpse of knowledge drawn from the mixed forces of our IR and MDR groups, however centered on the cohort of consumers with 500 workers or fewer, please see our sister publication, the 2024 Sophos Risk Report.)
And what do these organizations do? For a fourth consecutive 12 months, the manufacturing sector (25%) was the more than likely to request Sophos IR providers, adopted by data know-how (10%), retail (9%), and providers (9%). In complete, 26 totally different sectors are represented on this dataset. Additional data on the information and methodology used to pick circumstances for this report could be discovered within the Appendix.
Editor’s be aware: Since preliminary publication, a sentence within the part “Stats #2: To AD or to not AD: Lively Listing takes the stage” has been fastened to mirror that mainstream assist for Home windows Server 2019 resulted in January 2024.
Abstract of findings
As has change into the norm for many incident response-focused stories all through the trade, ransomware maintained its dominance as the highest assault sort in 2023, with 70% of investigations ensuing from a ransomware assault. Whereas there was some fluctuation on a quarterly foundation, starting from 62% to 80%, we consider that this yearly common is nicely throughout the margins of what’s possible ransomware’s background fee.
Assault Sorts
2023 Assault Sorts
Rely
%
Ransomware
108
70.13%
Community breach
29
18.83%
Knowledge extortion
11
7.14%
Knowledge exfiltration
2
1.30%
Enterprise e-mail compromise *
1
0.65%
Internet shell
1
0.65%
Loader
1
0.65%
DDoS
1
0.65%
Grand Complete
154
100.00%
Determine 1: As in earlier years, our Incident Response crew carried out extra investigations of ransomware circumstances than of another sort of assault in 2023. Nonetheless, our knowledge signifies a lot of assessments outdoors the dataset that conform to Sophos’ definition of enterprise e-mail compromise. Since simply considered one of these assessments resulted in a full investigation, they’re flippantly represented within the report dataset, however the authors of this report could select to publish findings regarding these assessments at a later date
Community breach, the perennial bridesmaid, retained its spot with a 19% incidence fee in 2023. Whereas we are able to’t make certain in all circumstances, there may be mounting proof that many community breaches are certainly unsuccessful ransomware assaults. For instance, we positively recognized 5 community breaches (17%) that have been the work of identified ransomware manufacturers. An fascinating statistic emerged when evaluating community breaches to ransomware assaults by quarter: In the course of the quarters the place ransomware was at its lowest prevalence – 67% in Q2 and 62% in Q3 – community breaches have been significantly above the yearly common, 21% in Q2 and 28% in Q3.
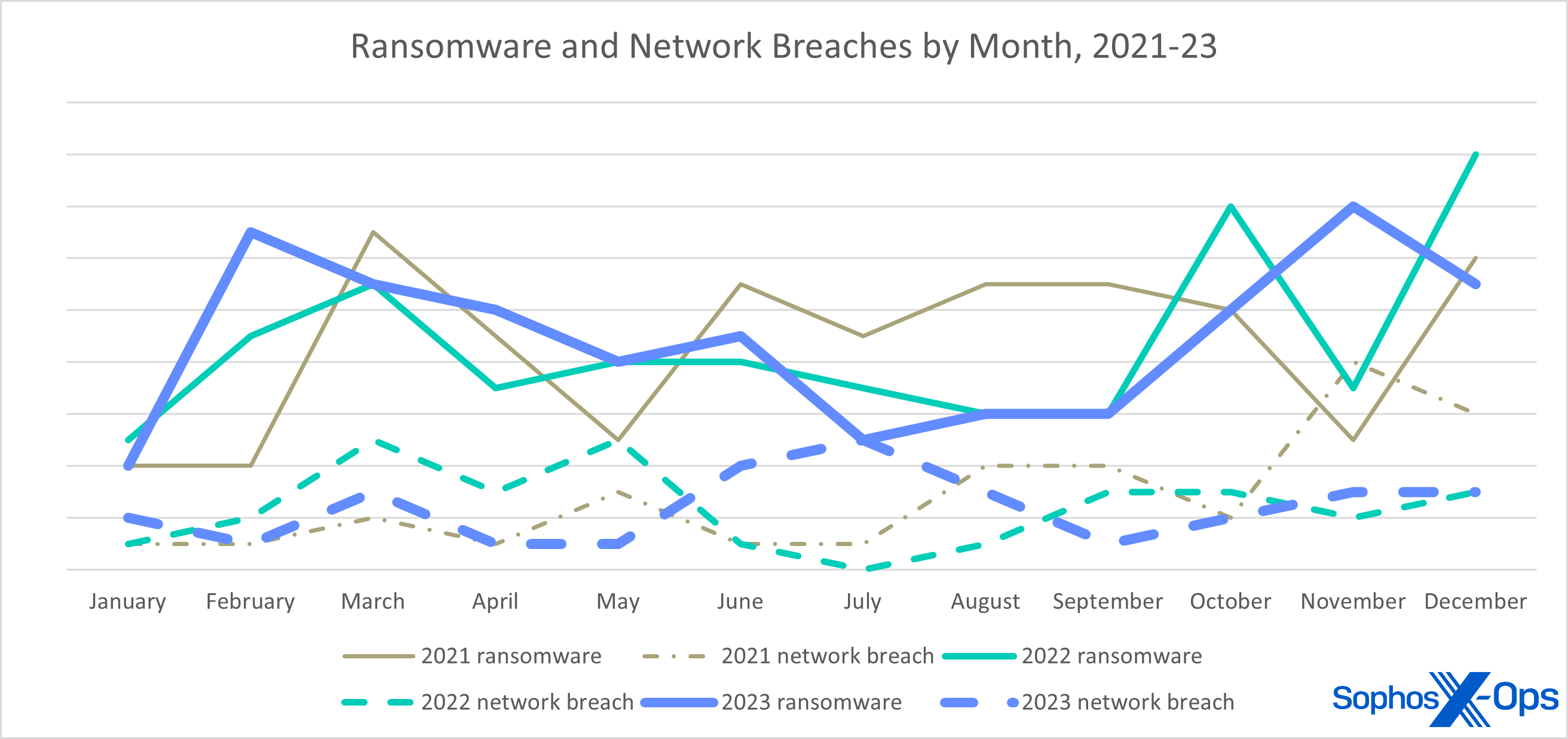
Determine 2: Throughout 2021 and 2022, cycles within the variety of ransomware circumstances and community breaches appeared to have delicate congruence – when ransomware was up, breaches have been usually up. In mid-2023, nevertheless, ransomware dropped simply as breaches spiked – not as placing because the full-on reversal of “fortunes” in November 2021, however maybe extra vital
What could be deduced about this from the information itself? Laborious to say with even medium confidence, nevertheless it’s potential that the set of victims throughout these two quarters have been higher ready to detect ransomware operators and evict them earlier than the actual harm was carried out, or the attackers have been distracted through the nicest time of the 12 months in Sochi.
The assault varieties which have seen essentially the most change in our dataset are knowledge extortion and knowledge exfiltration. We outline knowledge extortion as knowledge was stolen and a fee was demanded to suppress and/or delete it. Knowledge exfiltration omits the fee portion; the information was stolen and both uncovered to the general public or not. Our year-end tally noticed knowledge extortion assaults double over the earlier 12 months, with knowledge exfiltration assaults halving. A lot of the knowledge extortion assaults we investigated have been perpetrated within the first half of the 12 months by BianLian, which switched to extortion-only assaults in January 2023.
The remaining assault varieties for 2023 are enterprise e-mail compromise, net shell, loader, and DDoS. Every accounted for lower than 1% of investigated circumstances.
Impacts
2023 Influence
ATT&CK
Rely
% circumstances
Knowledge Encrypted for Influence
T1486
106
68.83%
(no influence)
N/A
29
18.83%
Inhibit System Restoration
T1490
29
18.83%
Monetary Theft
T1657
12
7.79%
Useful resource Hijacking
T1496
6
3.90%
Account Entry Removing
T1531
2
1.30%
Knowledge Destruction
T1485
1
0.65%
Community Denial of Service
T1498
1
0.65%
Grand Complete
186
Determine 3: Identified impacts of the 2023 circumstances; since one case could finally lead to a number of impacts, the whole is bigger than our case depend of 154
The result of assaults is the tactic (class) that the MITRE ATT&CK framework calls Influence (TA0040). It ought to come as no shock that the Knowledge Encrypted for Influence (T1486) method is main the pack: When ransomware is the number-one assault sort, this would be the number-one influence. As an adjunct to encryption, many attackers carry out different duties or deploy extra payloads that may be labelled. For instance, an often-observed epiphenomenon is the pairing of Inhibit System Restoration (T1490) with Knowledge Encrypted for Influence.
The subsequent most prevalent influence was what we name “no influence.” That is tightly coupled with community breaches. There isn’t a doubt in our minds, and we hope most will agree, that an attacker having privileged entry to your community constitutes some kind of influence. And, whereas MITRE’s methods cowl loads of floor, there isn’t a discrete method that adequately describes this phenomenon.
Notably, MITRE launched an replace to its framework in October 2023. One of many modifications was so as to add the Monetary Theft (T1657) method to the Influence tactic. A acknowledged motive for these modifications was for “encompassing extra actions which might be adjoining to, but result in direct community interactions or impacts.” It is a welcome addition because it permits us to correctly label the outcomes of knowledge extortion and exfiltration assaults, the place beforehand there was none.
Which segues properly to the subsequent most prevalent influence: Monetary Theft. The rise in this sort of knowledge extortion led to a commensurate doubling on this method, which overtook Useful resource Hijacking within the 2023 rating, whereas Useful resource Hijacking has dropped to one-third of its 2022 fee. This system is typically the results of attackers utilizing compromised techniques for spam campaigns, as is the case in lots of SquirrelWaffle infections, however most frequently the method denotes a coin miner being current on the community. (It’s unclear why coin miners are in decline, aside from the truth that they aren’t terribly profitable.)
Excluding one Community Denial of Service assault in opposition to an entity within the Training sector, the remaining methods in our dataset have been secondary impacts paired with ransomware assaults.
Attribution
2023 Attribution
Rely
%
LockBit
24
22.22%
Akira
12
11.11%
ALPHV/BlackCat
10
9.26%
Play
7
6.48%
Royal **
6
5.56%
Black Basta
5
4.63%
CryTOX
4
3.70%
BlackByte
3
2.78%
Staff Snatch
3
2.78%
Mario
3
2.78%
Rorschach
2
1.85%
Faust
2
1.85%
(unknown)
2
1.85%
BitLocker*
2
1.85%
Vice Society
2
1.85%
Phobos
2
1.85%
BlackSuit **
2
1.85%
Rhysida
2
1.85%
Prometheus
1
0.93%
Hunters Intl
1
0.93%
INC
1
0.93%
Cyclops
1
0.93%
Cuba
1
0.93%
8Base
1
0.93%
Cash Message
1
0.93%
HIVE
1
0.93%
RA Group
1
0.93%
Mimus
1
0.93%
FuxSocy
1
0.93%
d0nut
1
0.93%
NoEscape
1
0.93%
Qilin
1
0.93%
RansomEXX
1
0.93%
Grand Complete
108
100.00%
Determine 4: Household distribution of ransomware circumstances evaluated in 2023. For the entry marked with an asterisk, the attacker put in Home windows BitLocker providers to each encrypt information and take away quantity shadow copies. For the entries marked with two asterisks, there’s a chance these are the identical factor, as mentioned under
Few menace panorama analyses are full with out an attribution dialogue. Whereas we received’t preach at size over who was behind many of those assaults, we are able to current the info as we noticed them. Naturally, essentially the most dependable attributions come from ransomware assaults. It’s because the attackers let you know which model of ransomware was deployed in your community by means of file extensions (typically), ransom notes (all the time), and knowledge leak portals (generally). Like so many telemarketers, most ransomware manufacturers exist as ransomware-as-a-service choices, which permits criminals to symbolize multiple outlet.
LockBit maintains the highest spot for many prolific ransomware model of the 12 months for the second 12 months operating, lastly displacing Conti in our all-time rating. Multiple-fifth of ransomware assaults we investigated in 2023 deployed LockBit.
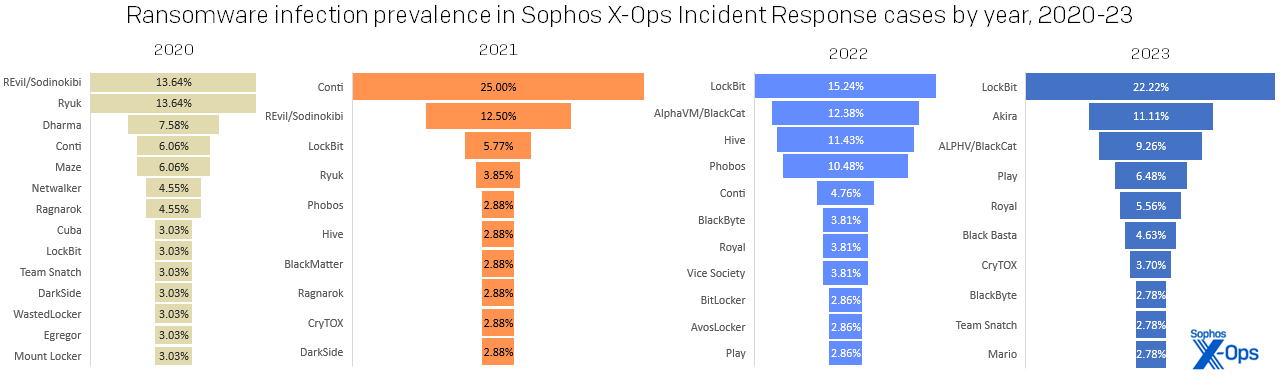
Determine 5: LockBit dominated the 2023 standings extra strongly than any single ransomware household has for the reason that heyday of Conti, in 2021; then as now, the second-place household represented a mere half of the chief’s complete
One notable entrant within the ransomware panorama was Akira. First launched in March 2023, this up-and-coming model positioned second in our rating, displacing different notable manufacturers like ALPHV/BlackCat, Royal (possible rebranded in 2023 as BlackSuit), and Black Basta. (Have been we to mix Royal and BlackSuit on our chart, it might be in fourth place within the rating.) However this degree of breakaway success doesn’t essentially imply infallibility. One of many circumstances we investigated as a community breach was discovered to be a failed Akira assault, as have been circumstances involving ALPHV, Black Basta, Everest, and Vice Society. Had these assaults succeeded, they’d have elevated the ransomware share to 73%, with a proportional drop within the community breach share.
The highest 5 ransomware manufacturers have been liable for over half (55%) of all ransomware assaults, which isn’t stunning contemplating the pedigrees of a few of these manufacturers. Akira and Royal have each been linked to the Ryuk department of ransomware households, which as many will know begat the Conti ransomware group and its many descendants. If we increase to the highest 10, we discover two extra of Conti’s alleged progeny, Black Basta (#6) and BlackByte (#8). Of the information extortion teams, we additionally discover that Karakurt has potential hyperlinks to this prodigious department. Even LockBit is said in a way, as a result of that group has been noticed utilizing a few of Conti’s code after the leaks in 2022.
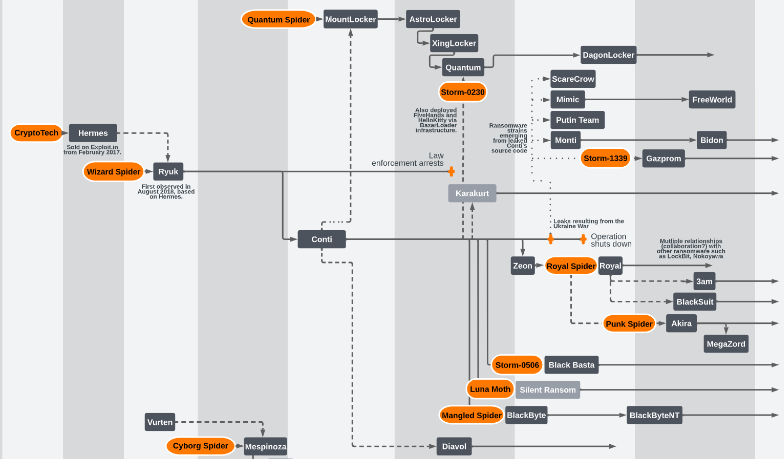
Determine 6: Fruits of a poisoned tree: Most fashionable ransomware households are associated to a couple “founding” entities, beginning with 2016’s CryptoTech; the uncertainty re the possible renaming of Royal to BlackSuit is mirrored at decrease proper. Supply: https://github.com/cert-orangecyberdefense/ransomware_map/blob/predominant/OCD_WorldWatch_Ransomware-ecosystem-map.pdf , of which this diagram is only a small portion
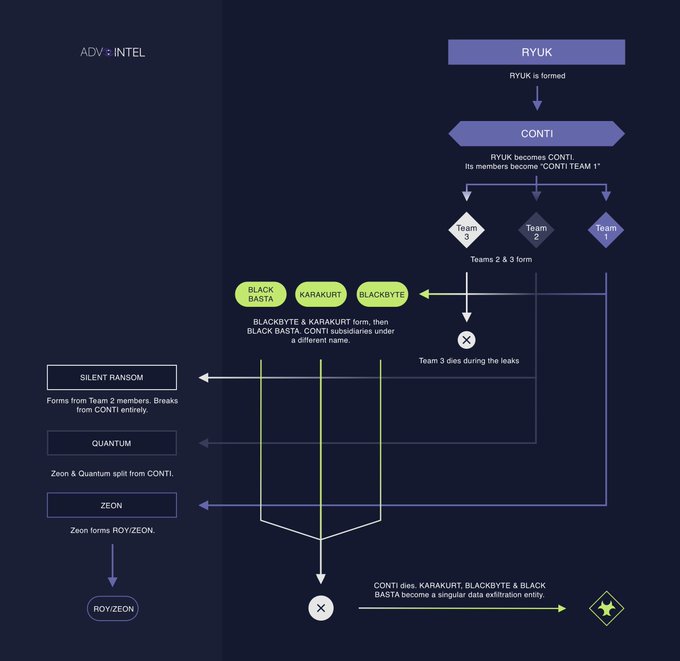
Determine 7: A more in-depth look from 2022 on the (considerably inbred) Conti household. Supply: https://twitter.com/VK_Intel/standing/1557003350541242369/photograph/1
It’s tempting to suppose that there’s one thing particular about these teams, however there isn’t. Fashionable ransomware turned 10 years outdated in mid-September 2023. The truth is that most of the people behind these teams have been lively for some time and have had loads of time and alternative to hone their expertise. For numerous causes, ransomware teams come and go, however we’ve additionally noticed just a few, specifically Cuba, LockBit, Phobos, and Snatch, which were a part of our investigations for the reason that first Lively Adversary report.
2023 Attribution (knowledge extortion circumstances)
Rely
% of circumstances
BianLian
8
72.73%
Cl0p
1
9.09%
Hunters Intl
1
9.09%
Karakurt
1
9.09%
Grand Complete
11
100.00%
Determine 8: BianLian dominated the data-extortion circumstances we noticed; although Cl0p made loads of headlines, its precise influence on our IR prospects was vanishingly small
Of the information extortion group, BianLian led the way in which, adopted by Cl0p, Hunters Worldwide, and Karakurt. The Hunters Worldwide assault was a failed ransomware assault, however having stolen knowledge, they resorted to knowledge extortion by demanding fee to suppress publication of the stolen knowledge.
Don’t name it a comeback — I been right here for years
Figuring out who attacked you may supply some emotional rescue, nevertheless it actually doesn’t matter — besides in a single situation. In case you intend to pay, it’s completely essential to discuss with authorized counsel beforehand, in case the ransomware group in query has been designated as a sanctioned entity by your authorities.
In any case, many ransomware assaults, whatever the branding on the ransom be aware, are perpetrated by the identical people or teams of people, they usually largely use the identical tooling and infrastructure. What issues most within the incident-response context is how the attackers breached the group and why they succeeded. This enables for full remediation and restoration.
Down within the Gap: Preliminary Entry and Root Causes
2023 Preliminary Entry
ATT&CK
2023 depend
% of 2023 circumstances
% of circumstances all-time
Exterior Distant Providers
T1133
100
64.94%
45.95%
Legitimate Accounts
T1078
78
50.65%
25.24%
Exploit Public-Going through Software
T1190
26
16.88%
25.05%
(unknown)
N/A
15
9.74%
7.34%
Phishing
T1566
6
3.90%
5.46%
Provide Chain Compromise
T1195
4
2.60%
0.75%
Trusted Relationship
T1199
3
1.95%
1.88%
Drive-by Compromise
T1189
2
1.30%
0.75%
Grand Complete
234
Determine 9: Preliminary entry strategies, when discernible in the middle of investigation, exhibited a little bit of range in 2023. As one would count on, some circumstances reveal a number of believable initial-access situations. Most importantly, of the 78 Legitimate Accounts circumstances we noticed, in just one was Legitimate Accounts the first technique; within the different 77, it was a contributing consider circumstances involving Distant Providers
2023 Root Trigger
2023 depend
% of 2023 circumstances
% of circumstances all-time
Compromised credentials
86
55.84%
33.33%
Exploit vulnerability
25
16.23%
29.76%
(unknown)
20
13.64%
18.27%
Brute drive assault
6
3.90%
3.01%
Phishing
5
3.25%
5.65%
Provide chain compromise
4
2.60%
1.13%
Malicious paperwork
4
2.60%
3.20%
Adware
2
1.30%
0.56%
Auth token theft
1
0.65%
0.19%
Grand Complete
154
100.00%
Determine 10: As for root causes, compromised credentials high the full-year charts for the primary time ever in 2023
The MITRE tactic and the related methods that describe how an attacker managed to infiltrate the goal are grouped underneath Preliminary Entry (TA0001), whereas Root Causes, which do not need formal ATT&CK designations, describe why that method labored. For instance, if the attackers infiltrated the community by means of an exterior distant service, comparable to a VPN, that may be how they bought in. However the root trigger — why that method labored — was possible as a result of compromised (stolen) credentials (in MITRE ATT&CK terminology, Legitimate Accounts). We’d argue that on this instance, each Exterior Distant Providers and Legitimate Accounts offered preliminary entry, with compromised credentials performing as a root trigger. Whereas the 2 typically line up, we nonetheless prefer to separate them so we are able to higher perceive how the assault succeeded, which informs remediation and protection.
As has been the case for each Lively Adversary report thus far, Exterior Distant Providers (T1133) was the main preliminary entry technique. In 65% of circumstances, some kind of distant entry know-how facilitated the intrusion; be {that a} VPN system or an uncovered Distant Desktop Protocol (RDP) service, the attackers had a goal of alternative. All that remained was determining the way to make the most of this chance.
One method to train that chance is by utilizing Legitimate Accounts (T1078). Over three-quarters (77%) of assaults noticed compromised credentials as an preliminary entry technique and over half (56%) as a root trigger. Typically, we don’t know the way the accounts have been compromised, however we do know that the attackers walked by means of the entrance door utilizing a sound username and password.
It seems that the majority circumstances in 2023 noticed that pairing of preliminary entry and compromised credentials. We famous in our earlier report that compromised credentials had rocketed to the highest of the Root Trigger charts within the first half of 2023. Now that now we have an entire dataset for 2023, we see that the development holds, practically doubling final 12 months’s complete.
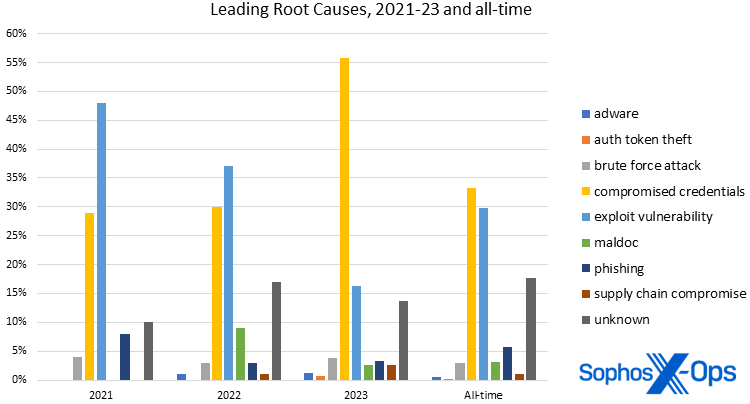
Determine 11: The astonishing rise of compromised credentials as a root explanation for assaults vaulted the (largely avoidable) downside to the highest of the all-time charts in addition to 2023’s
What makes this worse is the woeful state of credential hardening. In 43% of investigations, multi-factor authentication (MFA) was not configured. (As a reminder, MFA is know-how that’s practically three many years outdated at this level; one of many founding patents actually offers an implementation instance involving two-way pagers.)
The remaining root causes for assaults involving distant providers have been brute drive assaults (6%), unknown (3%), phishing (3%), and exploits (2%).
Contemplating compromised credentials’ ascendency, plain outdated vulnerability exploitation has due to this fact slipped to second place. As now we have written beforehand, this isn’t irrefutable proof that attackers have gone off utilizing vulnerabilities. Perhaps there weren’t as many simply exploitable vulnerabilities as there have been in earlier years. Or perhaps preliminary entry brokers had loads of stock on their fingers that they wished to eliminate cheaply. Regardless of the case, attackers will select the trail of least resistance, and for 2023, that meant utilizing compromised credentials.
Past the highest “three” (because it’s debatable how helpful “unknown” as a class is to investigators, even when the contributors to the class are identified), the remaining recognized root causes – brute drive assault, phishing, provide chain compromise, maldocs, adware, and authentication token theft – accounted for a mixed 14% of findings. The Unknown class is the third commonest “motive” for each preliminary entry and root trigger, and the largest contributor in each circumstances was lacking telemetry. Whether or not the logs have been cleared by the attackers or worse, not configured, our investigators have been unable to find out key elements of the assault. Frankly, in 2023 compromised credentials and exploited vulnerabilities have been the ball sport.
Hey child – it’s the stats, man!
With the adversary panorama in a comparatively calm interval at this writing, let’s take a second to consider, because the Lively Adversary report crew typically says, how we all know what we all know. To make sure we’re getting the utmost good out of all the information we provide in these stories, let’s discuss statistics and what they will present – or disguise. We’ll first study the exceptional drop in dwell occasions that we coated all through 2023 to see what else we would be taught from another have a look at these numbers. Subsequent, we’ll have a look at time-to-Lively Listing, a statistic we began monitoring solely final 12 months, to see how evaluation helps us see that image because it develops. After that, we’ll study a subject the place lack of essential knowledge leaves researchers in an ungainly place, and shut this part with a have a look at a statistic that fell unexpectedly out of the dataset in the course of final 12 months and nonetheless has us asking questions.
Stats #1: Assault timelines: Time is in your facet (till it’s not)
After we printed our first Lively Adversary report in 2021 (based mostly on 2020 knowledge), dwell time was a kind of measures that sparked loads of curiosity. Again then we have been used to interested by dwell time in weeks and months, however we have been capable of present that the median dwell time, particularly for incident response circumstances, was measurable in days. 
Within the subsequent report (based mostly on 2021 knowledge), we noticed dwell time rise and attributed this to the emergence of Preliminary Entry Brokers (IABs), which offered a buffer between the earliest compromise and the eventual assault.
Then the decline began — by a bit in 2022, then by quite a bit in 2023. The primary quarter of 2023 (which included knowledge by means of the tip of 2022) was enterprise as typical, with dwell time equaling that of the earlier 12 months. By the point we launched our remaining report in 2023 (which included Q1-Q3 knowledge), dwell time had halved. By the point we wrapped up the 12 months issues had stabilized. As is usually the case, understanding the main points is necessary.
2023 Incident Dwell Occasions (by quarter)
2023
Minimal
Most
Imply
StdDev
Median
Q1
0
112
18.69
24.06
10.00
Q2
0
73
12.37
15.66
7.00
Q3
0
114
16.86
31.18
5.00
This fall
0
289
23.76
49.33
8.00
Full 12 months
0
289
18.18
33.08
6.00
Determine 12: The dwell-time numbers wobbled a bit all through 2023, however nonetheless landed firmly under the earlier median dwell time of 10 days
One motive we select to have a look at dwell time (and plenty of different measures) utilizing its median worth is to cut back the influence of outliers. For instance, in 2022 we had a case with a professional dwell time of 955 days. If we examine this dataset with one which omits that case, the imply reduces by a bit over 6 days, however the median is unaffected.
What a Distinction a Case Makes
2022’s extraordinary outlier and the way it affected dwell statistics
Minimal
Most
Imply
StdDev
Median
With outlier
0
955
36.99
95.32
10.00
With out outlier
0
345
30.78
58.11
10.00
Determine 13: A single extraordinary outlier within the dataset may cause outsized distortion within the numbers, which is why we like to have a look at median values
One other worth that we monitor, however don’t normally draw a lot consideration to, is the usual deviation of a dataset. Put merely, the usual deviation measures the unfold or variability of knowledge from its imply. Utilizing the dataset in Determine 13 for example, we additionally expertise a dramatic reducing of the usual deviation in dwell time, from 95.32 days to 58.11 days, after we omit the outlier. In different phrases, the set of values that make up the information are nearer to the imply.
The issue with some outliers is that they will obscure patterns within the knowledge. With this in thoughts, we examined the dwell time knowledge for the previous three years, whereas controlling for the outlier in 2022 as proven above:
Attacker Dwell Time Statistics (with 2022 outlier case eliminated), 2021-23
Dwell time
Minimal
Most
Imply
StdDev
Median
2021 (n=144)
0
411
41.69
59.65
13.00
2022 (n=148)
0
345
30.78
58.11
10.00
2023 (n=147)
0
289
18.16
33.08
6.00
Determine 14: Having eradicated the impact of the outlier from the 2022 knowledge, the year-to-year development of lowering dwell occasions turns into clear
We posited in a earlier report that shrinking dwell occasions have been possible as a result of a number of components, together with elevated detection capabilities, and that attackers have possible sped up in response.
Along with shrinking median dwell time, we additionally noticed, as we see in Determine 14, the remaining values declining regardless of equally sized populations. Issues get much more fascinating after we separate ransomware from all different assault varieties:
Dwell Time in Ransomware Assaults, 2021-23
Minimal
Most
Imply
StdDev
Median
2021
0
190
29.88
42.29
11.00
2022
0
292
23.80
45.42
9.00
2023
0
146
15.92
25.53
5.00
Dwell Time in Non-Ransomware Assaults, 2021-23
Minimal
Most
Imply
StdDev
Median
2021
1
411
72.38
83.58
52.50
2022
0
345
45.79
77.25
10.00
2023
0
289
23.22
45.79
10.00
Determine 15: Once more with the 2022 outlier dismissed from the information, we see that the lower in dwell occasions applies to each ransomware infections and (to a lesser extent) all different assault varieties
It makes intuitive sense that ransomware attackers would spend much less time than different sorts of attackers inside networks. In the present day it appears a few of these attackers rely much less on particular person payouts and extra on quantity. (That is apparently figuring out for them; in response to statistics printed earlier this 12 months by Chainalysis, payouts for 2023 possible surpassed $1 billion USD.) The assaults themselves could be noisy, particularly when payloads are launched into the community. In distinction, net shell implants and coin miners are supposed to be stealthy and protracted.
Measuring dwell time and commenting on its that means has been a fixture of this report since its inception. We’ve included it right here for completeness, however like many elements of the menace panorama and attacker conduct, we predict dwell time has reached stasis. It’s unlikely that these dwell time values will change dramatically within the brief time period. Like ransomware prevalence, there is likely to be some variability from 12 months to 12 months, however the general development will stay steady, and it’ll in fact by no means attain zero.
Dwell time is a lagging indicator. It could possibly solely be calculated after the intruders have been found. One method to shrink dwell time is to detect intrusions sooner, and there are different time-based indicators that may assist defenders spot suspicious exercise within the community – if, in fact, you’re looking ahead to that kind of factor.
Stats #2: To AD or to not AD: Lively Listing takes the stage
In 2023, to higher perceive attacker timelines, we began capturing the time-to-Lively-Listing (AD) metric. What we discovered is that the median time-to-AD for all assaults in 2023 was 0.64 days. The earliest time-to-AD was –28.90 days, whereas the longest was 281.45 days. This contrasts with the time distinction between having access to an AD server and when the assault is detected: Right here we noticed a median of two.02 days.
The place accessible, we additionally recorded the working system model of affected AD servers. This may be vital since Microsoft steadily improves the baseline safety of AD over subsequent releases. We discovered that 90% of AD servers have been operating Home windows Server 2019 – which exited mainstream assist in January 2024 – or earlier variations. (The case dataset included three deployments of Home windows Server 2008.) We additional famous that 79% of AD servers have been protected solely with Home windows Defender, and a minimum of two servers had no safety in anyway.
Typically, as all researchers will let you know, what appears fascinating in a smaller dataset will get overturned by inspecting a bigger one. Since no good deed goes unpunished, we went again to gather the time-to-AD knowledge from the 152 circumstances investigated in 2022 so we might perceive the larger image and examine the values. Because it was for dwell time, the 2022 median time-to-AD was 1.34 days — greater than double the median for 2023. The earliest time-to-AD was -208.29 days (sure, a unfavourable quantity; in that case, the client skilled an AD compromise that lengthy predated different artifacts associated to their community breach) and the longest was 140.64 days. In 2022, 98% of AD installations have been Home windows Server 2019 or earlier, and 69% have been protected with Home windows Defender.
Armed with the information that some attackers are making a mad sprint for Lively Listing servers, we have to be ready to detect them post-haste. A part of that preparation consists of having the correct options in place to detect suspicious exercise, the folks accessible to analyze suspicious alerts, and the required telemetry to find out what occurred.
Transferring previous the required grind of statistics, we flip our consideration now to…
Stats #3: Exfiltration (you don’t know what it’s bought ‘til it’s gone)
Knowledge theft is one other alternative for detecting an intruder. When confronted with knowledge exfiltration or knowledge extortion, time has already run out. Nonetheless, when dealing with a ransomware assault, there may be nonetheless a chance to detect the intruders and evict them from the community earlier than they proceed to the ultimate act.
All-cause knowledge exfiltration occurred at roughly the identical fee in 2023 because it did in 2022. We might verify exfiltration in 40% of circumstances; an extra 14% had indications of potential exfiltration or of knowledge staging (an exercise one would count on to see in the middle of an exfiltration try). The earlier 12 months noticed 43% confirmed exfiltrations with an extra 9% decided as potential knowledge theft.
One other space the place lacking logs hampers investigations is in figuring out whether or not exfiltration has occurred. In 42% of circumstances, incident responders have been unable to find out from the accessible proof whether or not any exfiltration had occurred. This was largely as a result of there being no proof accessible for responders to substantiate or deny whether or not exfiltration occurred. Breaking it down additional, of the 55 circumstances missing adequate proof, 29 circumstances (53%) have been lacking logs and an extra 6 circumstances (11%) had logs erased by the attackers.
For ransomware assaults we might verify knowledge exfiltration in 44% of circumstances, with an extra 18% displaying potential knowledge exfiltration or knowledge staging. Sadly, we have been unable to find out if knowledge was stolen in 30% of circumstances. Of these circumstances, 69% have been hampered by lacking logs, with 56% as a result of lacking logs and 13% as a result of cleared logs.
Alarmingly, 72% of community breach investigations discovered no proof of knowledge exfiltration. Greater than half of the lacking proof was as a result of lacking (43%) or deleted (14%) logs.
There’s an inverse relationship between time-to-AD and knowledge theft. The place attackers rush to get entry to AD, the information exfiltration element of a ransomware assault seems to return on the finish of the marketing campaign. For instance, within the 2023 knowledge, the median time between the beginning of the assault and the deployment of a ransomware payload in a confirmed exfiltration was 3.76 days. In distinction, the time between exfiltration and deployment was 0.6 days.
As with time-to-AD, this metric is simply helpful if a corporation has the required components in place to detect and reply to a knowledge exfiltration occasion. If exfiltration is the last word aim of the attackers, the group can rapidly decide their publicity and start the method of notifying regulators and different stakeholders. As governments world wide improve their guidelines and laws regarding knowledge breaches, sufferer organizations might want to reply in type. If the exfiltration occasion is a precursor to a ransomware assault, detecting a knowledge exfiltration occasion might imply the distinction between a foul day on the workplace and a really unhealthy day within the information.
Stats #4: Ransomware’s evening strikes
Some of the stunning outcomes from our knowledge evaluation for the mid-year report in 2023 was a robust sample within the native time of day when ransomware was deployed. For that report, the dataset included all circumstances from the primary half of 2023. Evaluation confirmed that 91% of ransomware payloads have been deployed outdoors of conventional enterprise hours. As we did for time-to-AD, we eagerly awaited the full-year knowledge to see if the outcomes can be upheld by a much bigger dataset, since (as famous above) bigger datasets typically expose biases in knowledge and results can get watered down. Whereas we waited, we re-examined the information and corrected for nations the place enterprise days aren’t historically Monday to Friday. (The unique evaluation assumed the “workweek” to be 5 commonplace working days of 8am to 6pm, Monday by means of Friday; the “weekend” was held to be the interval between 6pm on Friday and 12am on Monday.)
Whereas there was a small correction utilized by doubling the dataset, we discovered that 90% of ransomware deployments have been deployed outdoors of enterprise hours in 2023. A complete of 11 assaults have been launched throughout native enterprise hours within the workweek.
Since we have been already re-analyzing circumstances for time-to-AD, we additionally tried to seize the ransomware deployment time for 2022. What we discovered was that 94% of ransomware deployments occurred outdoors of enterprise hours. Solely six circumstances fell inside workplace time.
Whereas we received’t contemplate these outcomes definitive – we don’t have visibility into each ransomware assault – we are able to pronounce with excessive confidence that ransomware deployments are most prevalent outdoors of conventional enterprise hours. When each 2022 and 2023, 92% of ransomware assaults assist this discovering.
One factor we are able to conclude by analyzing attacker timelines is that point could be on our facet throughout an assault. Regardless of shrinking dwell occasions, defenders nonetheless have a median 6 days to detect an intruder. Nonetheless, these occasions change dramatically when a motivated actor strikes. Within the case of ransomware in 2023, the median time shrinks to five days, versus 10 days for all different assault varieties.
As well as, there are indicators alongside the way in which that may alert defenders to a possible hazard lurking within the community. Instantly detecting an intruder on an Lively Listing server can imply stopping an assault in lower than 24 hours. Recognizing a knowledge exfiltration occasion can stop an much more devastating end result.
We all know that by means of years of observe many ransomware criminals have honed their expertise. However this isn’t a one-way battle. Defenders can even sharpen their expertise by training response playbooks – and, as this part has proven, by the true understanding of what the statistics are saying.
Identical because it ever was: Artifacts, LOLBins, and different findings
Turning our consideration from the statistics to the standard examination of instruments and techniques, methods, and procedures (TTPs), analyzing this 12 months’s crop evokes robust emotions of déjà vu. We noticed the identical objects in every high 5, albeit in barely totally different orders, year-on-year. It’s not till we glance previous the highest ten that we begin seeing variability. Nowhere is that this stasis extra obvious than within the instruments used and abused by attackers up to now three years. In each the detected instruments and Microsoft binaries, the highest ten are practically an identical. It’s nearly as if the attackers aren’t being challenged and might merely re-use the identical instruments and TTPs advert infinitum.
Artifacts
Most Generally Encountered Artifacts of 2023
2023 Artifacts
2023 depend
% of circumstances 2023
% of circumstances all-time
SoftPerfect Community Scanner
51
33.12%
22.79%
Cobalt Strike
41
26.62%
38.61%
AnyDesk
40
25.97%
23.16%
Superior IP Scanner
39
25.32%
20.72%
mimikatz
37
24.03%
26.93%
Impacket
34
22.08%
5.27%
WinSCP
28
18.18%
10.17%
Rclone
24
15.58%
13.37%
PuTTy
23
14.94%
11.30%
7zip
20
12.99%
9.42%
WinRAR
20
12.99%
11.86%
Determine 16: SoftPerfect Community Scanner leads the checklist of artifacts noticed in 2023 IR circumstances, displacing Cobalt Strike from the perch it has held for the reason that begin of the Lively Adversary Report sequence; nevertheless, Cobalt Strike nonetheless leads the all-time incidence checklist
Regardless of the highest instruments being related year-on-year, there may be one development which may sign a change in attacker conduct. Cobalt Strike, the longstanding chief, has seen its share decline steadily up to now three years. Whereas it nonetheless maintains the highest spot within the all-time rankings by absolute depend, the proportion of assaults utilizing a Cobalt Strike payload has declined considerably; within the interval from 2021 to 2023, the share of Cobalt Strike has gone from 48% to 27%. A possible motive for that is that Cobalt Strike has been so closely abused that now we have change into very adept at detecting and blocking it.
The general chief this 12 months was SoftPerfect’s Community Scanner, which is routinely abused by attackers to map out networks and uncover potential targets. We’ve seen abuse of this software program for a few years and its utility hasn’t gone unnoticed by the attackers. One other incessantly abused, albeit professional, utility is AnyDesk, the favored device for directors to handle their endpoints.
One fascinating ingredient of the highest 10 is that fifty% of the instruments facilitate knowledge exfiltration. Each 7zip and WinRAR (once more, instruments with professional makes use of, however abused by attackers) are routinely used to create archives that allow and probably obfuscate knowledge theft, whereas the others allow the gathering and switch of stated archives. Sadly, many organizations nonetheless don’t have a agency sufficient grasp on what regular appears like, so that they miss giant transfers of knowledge leaving their community. (For instance, the MEGA cloud storage service is all too typically abused by knowledge exfiltrators; if in case you have site visitors both coming from or going to MEGA and you haven’t any pre-existing enterprise relationship with the corporate, that’s price investigating.)
An fascinating facet be aware is the incidence of the device Impacket in our dataset. As described by the maintainer of the undertaking: “Impacket is a set of Python courses for working with community protocols.” As this can be a assortment of instruments, we document their particular person use (e.g. Impacket/atexec, Impacket/secretsdump, Impacket/smbproxy, and many others.) to higher perceive how every is utilized in an assault. Nonetheless, if we roll all the person instruments into one “Impacket” knowledge level, a major consequence emerges. All makes use of of Impacket in 2023, counted collectively, would rank sixth within the artifacts checklist.
With few exceptions, a lot of the instruments on this class are prime candidates for monitoring and blocking.
MS-LOLBins
Most Generally Encountered Microsoft LOLBins of 2023
2023 MS-LOLBins
Rely
% of circumstances 2023
% of circumstances all-time
RDP
139
90.26%
83.80%
PowerShell
120
77.92%
71.94%
cmd.exe
83
53.90%
29.94%
web.exe
60
38.96%
26.93%
PsExec
60
38.96%
43.88%
Activity Scheduler
55
35.71%
25.99%
rundll32.exe
43
27.92%
22.79%
ping.exe
41
26.62%
15.63%
nltest.exe
31
20.13%
10.73%
reg.exe
31
20.13%
12.62%
Determine 17: RDP continues to rule the MS-LOLBin roost, with PowerShell the fixed runner-up
Distant Desktop Protocol (RDP) is as soon as once more essentially the most abused of all of the Microsoft LOLBins (living-off-the-land binaries). We received’t spend a lot time discussing RDP on this report – as a substitute, please see our particular supplemental protection, which fits into each statistics and suggestions for coping with the protocol — however we do suppose it’s on monitor for a lifetime achievement award. RDP abuse has reached new heights, with 90% of assaults utilizing it for inner lateral motion and 20% for exterior distant entry. As for the 18% of organizations who nonetheless have RDP uncovered to the web, it is best to ask your self, “My God, what have I carried out?” (To learn the way that has labored out for one Sophos buyer, preserve studying; this report’s Case Research part is simply forward.) At publication time, there have been roughly 4 million uncovered RDP techniques on the web.
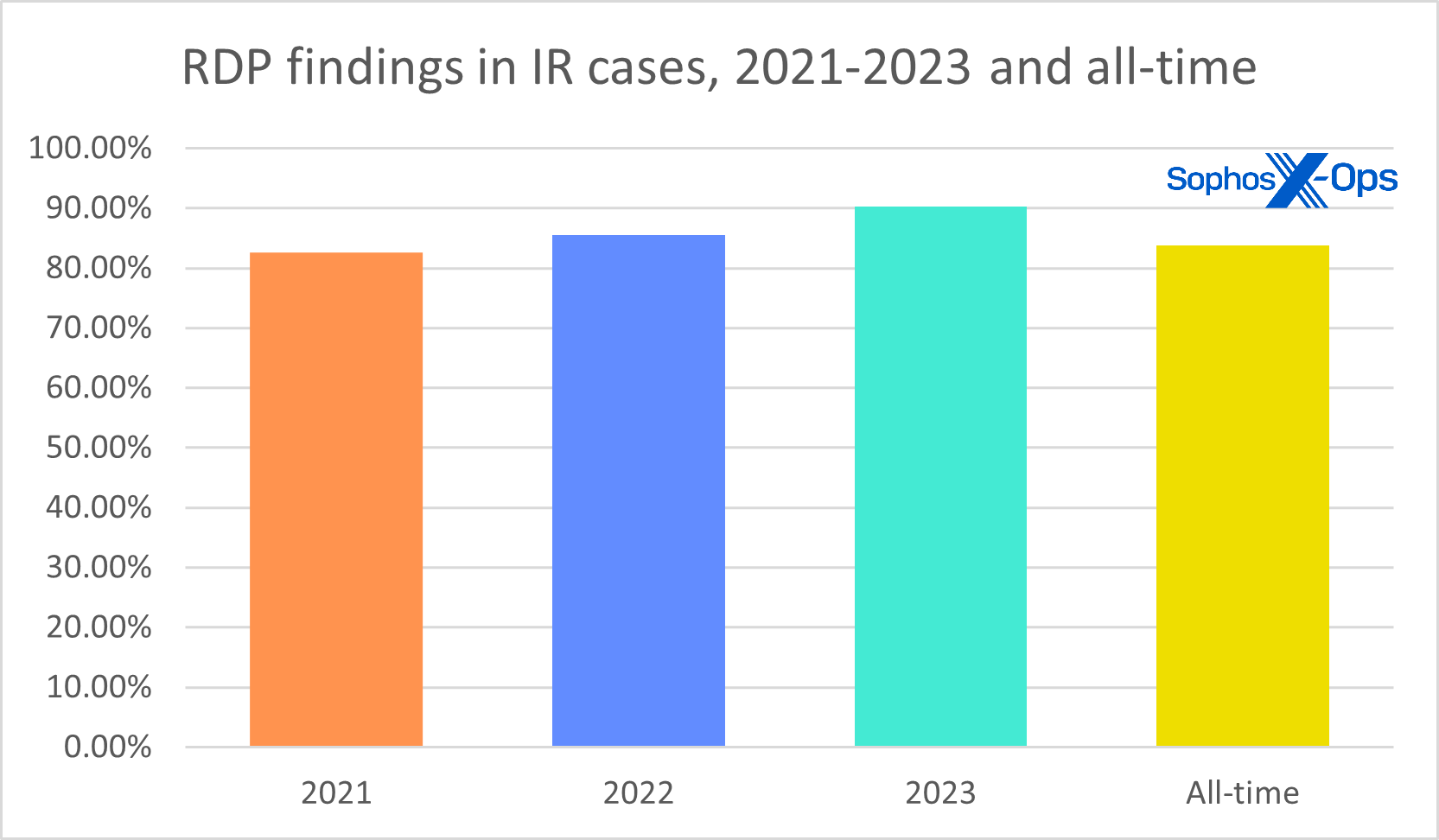
Determine 18: In 2023, 9 out of ten assaults dealt with by our IR crew included proof of RDP abuse
Setting RDP apart, PowerShell continues to energy many assaults as a result of its ubiquity, privilege, flexibility, and usefulness. It’s troublesome to argue for its removing from networks; due to this fact, the one choice is to strictly monitor and management it. Methods for utilizing PowerShell safely and securely embrace (however aren’t restricted to): logging all PowerShell exercise, making use of the precept of least privilege to which accounts can run scripts, operating the most recent model, and enabling constrained language mode.
The remainder of the binaries on this checklist are used for numerous functions, together with execution, persistence, protection evasion, discovery, and lateral motion. Having visibility into all of your gadgets and the capability to behave when obligatory is a requirement for at the moment’s defenders.
Different
Most Generally Encountered Different Findings of 2023
2023 different
Rely
% of circumstances 2023
% of circumstances all-time
legitimate accounts
122
79.22%
44.26%
set up service
92
59.74%
42.56%
logs lacking
83
53.90%
17.89%
browse community
79
51.30%
28.06%
malicious scripts
73
47.40%
50.09%
disable safety
73
47.40%
30.70%
MFA unavailable
66
42.86%
19.96%
create accounts
52
33.77%
20.72%
logs cleared
49
31.82%
22.03%
modify native teams
35
22.73%
9.98%
lsass dump
35
22.73%
17.33%
Determine 19: A historically extra unstable class than both Artifacts or LOLBins, the catchall Different class has been led for 2 years now by Legitimate Accounts; it was preceded in 2020 and 2021 by Malicious Scripts
The methods and different indicators that we noticed this previous 12 months are additionally very a lot commonplace working process for a lot of assaults. This part of our findings knowledge is normally the place we see essentially the most variability. For instance, we use this class to trace particular exploits which might be getting used within the wild, and people typically change from 12 months to 12 months, however these largely make up the lengthy (>200) tail of this dataset. Entrance and middle are methods and observations that contribute to the fog of conflict that surrounds many investigations.
A number of phrases about lacking and cleared logs, a subject we’ll sort out extra totally in a later Lively Adversary publication: Attackers have change into adept at disabling safety and clearing their tracks. This concerted effort to blind defenders is normally within the service of remaining undetected. Nonetheless, there are unintended penalties to disabling safety that may be to a defender’s benefit. A telemetry sign going darkish needs to be a beacon that one thing is going on within the surroundings which requires rapid consideration.
By no means thoughts attackers attempting to blind us; in lots of circumstances we’re blinding ourselves.
In 2023 we began capturing the incidence of lacking telemetry, for the reason that knowledge confirmed that this was the case in 54% of assaults we investigated. What was most stunning was how prevalent this new metric turned out to be: In its first 12 months of AAR scrutiny, it cracked the highest 10 in our all-time rating. Whereas there have been a number of the explanation why the logs have been unavailable, typically it was as a result of organizations hadn’t taken the required steps to make sure they’d be there when it mattered most.
And, as if the overwhelming quantity of credential compromise wasn’t sufficient, 43% of organizations had uncared for to allow MFA on their exterior providers. There isn’t a different method to put this: When an answer exists that may cease an attacker of their tracks, and it’s not carried out, it’s willful negligence. Within the remaining part of our report, we’ll have a look at how that labored out for a particular MDR buyer.
Case research: You bought one other factor comin’ (and one other and one other and)
Time and again within the Lively Adversary report sequence, we’ve repeated three elementary safety ideas – primary hygiene for defenders. Right here they’re once more in large-print haiku type:
Why will we preserve hammering away at this? As a result of these three safety tenets nonetheless aren’t universally adopted, and we see the outcomes. One explicit MDR buyer final 12 months realized this the onerous approach, falling sufferer to compromise 4 occasions inside a six-month interval. With enterprise necessities stopping the client from addressing the basis trigger, the attacker gained preliminary entry by means of the identical vector every time – brute drive assaults in opposition to uncovered RDP ports. We’ve modified a number of the particulars to guard the client’s id, however we provide a 12 months within the lifetime of their story to encourage our readers to keep away from this destiny by prioritizing primary safety hygiene.
December 2022 (prologue): Preliminary entry occurred by way of profitable brute drive assaults in opposition to a number of uncovered RDP ports. The attacker leveraged a number of PowerSploit modules and Rubeus tooling to compromise authentication, earlier than dropping plenty of malicious binaries and downloading an EDR-killer device. Sophos MDR’s response actions rapidly contained the menace. Nonetheless, the client declined the MDR suggestion to limit entry to uncovered RDP ports, citing enterprise wants.
Suggestions: After this case, MDR beneficial the client shut numerous RDP ports uncovered to the web; the client declined, citing enterprise wants. (A suggestion for domain-wide credential reset was not addressed; a patching suggestion was likewise unaddressed.)
Summer season 2023: Preliminary entry was once more achieved by means of profitable brute drive assaults in opposition to uncovered RDP ports. The attacker then created and leveraged the open-source PAExec device to run Nltest instructions to enumerate area controllers throughout the property. Following enumeration, the attacker moved laterally and modified registry values to allow Distant Desktop connections, permit unsolicited distant help requests, and disable Community Layer Authentication for RDP.
Suggestions: After this case, MDR reiterated the sooner suggestion that the client shut the uncovered RDP ports, and in addition beneficial that the client allow multifactor authentication, particularly if the RDP ports have been nonetheless required to be uncovered. The shopper once more declined the port suggestion and acknowledged that MFA choices have been underneath enterprise evaluate.
By means of December 2023: About 5 months later, a welter of assaults hit at roughly two-week intervals, every triggering a contemporary spherical of response engagements. Preliminary entry every time was achieved by brute drive in opposition to uncovered RDP. As soon as once more, following preliminary entry, the attackers carried out enumeration, moved laterally and modified registry settings to cut back restrictions on RDP entry. Response actions have been taken swiftly; nevertheless, investigators discovered a publicly uncovered worker net portal with no MFA. In the meantime, six ports first recognized a 12 months earlier have been nonetheless uncovered to the web. Regardless of MDR’s persistent suggestions, inner enterprise necessities continued to stop the client from implementing the suitable safety measures, leaving them weak to ongoing focusing on by menace actors utilizing brute drive assaults.
January 2024: Two weeks later, the client greeted the brand new 12 months with one other assault by way of the identical open ports. The timeframe of this report ends right here, however in all chance the assaults on the client didn’t. The client’s enterprise necessities don’t permit them to limit entry to uncovered RDP, nor have they enabled MFA; underneath these circumstances, there’s not a lot barrier to wave upon wave of additional assaults, nor a lot additional recommendation incident responders can supply them.
Threat acceptance is as much as each group individually; there isn’t a one-size-fits-all for threat administration. Nonetheless, when the danger as accepted leaves you regularly combating fires in all instructions, it’s in all probability time to reassess. Irrespective of how a lot the remainder of your defenses are tightened, with out following primary safety ideas, the group will persistently be left defending in opposition to menace actors whose preliminary entry might have been stopped on the first hurdle.
Conclusion
Trying again on 2023’s knowledge we’re left with a sense that not sufficient is being carried out to guard organizations from hurt. Certain, some companies could have the required protections in place, however nobody is paying consideration. Typically, the only variations between organizations which might be breached and ones that aren’t are 1) the preparation entailed by choosing and placing the correct instruments in place and a couple of) the information and readiness to behave when required.
Ransomware assaults have reached a stasis level with respect to prevalence, tooling, and timelines. Sadly, we’re additionally nonetheless seeing the identical errors being made by defenders yearly. It’s with this in thoughts that we predict organizations must urgently take part in their very own rescue. No trade, product, or paradigm is ideal, however we’re nonetheless combating yesterday’s battles with, too typically, the day earlier than yesterday’s weaponry. A lot of the instruments and methods described on this report have options, or on the very least, mitigations to restrict their hurt, however defenses are merely not maintaining.
Stolen credentials and unpatched techniques needs to be a statistic from a bygone period. Unprotected techniques, overprivileged customers, and uncontrolled purposes are issues which have options. Lacking telemetry might not be totally the fault of the victims (decided attackers will proceed to make defenders’ work tougher by interfering with that), however inadequate logging, or no logging in any respect, is an unintended oversight at greatest and a deliberate failure to behave at worst. These are all unforced errors, they usually should cease now.
A retrospective evaluation comparable to this, particularly throughout a comparatively quiet second within the wrestle, is a chance to be taught from earlier errors. It may be tempting to have a look at our failings and get offended that we aren’t progressing like we must always. We are saying: Don’t look again in anger — look ahead to how one can make optimistic change at the moment for a greater tomorrow.
Acknowledgements
MDR’s Hilary Wooden co-authored this report’s case research (“You bought one other factor comin’ [and another and another]”); Lee Kirkpatrick contributed the Lively Adversary Particular Report on RDP (“Distant Desktop Protocol: The Collection”) to which this report makes in depth reference. The authors want to thank Chester Wisniewski for his insights through the evaluation course of. Determine 6 was excerpted with thanks from work launched in 2023 by World Watch – World CERT – Orange Cyberdefense. Particular acknowledgement for Determine 7, which is the work of the late Vitali Kremez. He’s enormously missed.
Appendix: Demographics and methodology
As we put collectively this report, we selected to slender our focus to 154 circumstances that may very well be meaningfully parsed for helpful data on the state of the adversary panorama as of the tip of 2023. Defending the confidential relationship between Sophos and our prospects is in fact our first precedence, and the information you see right here has been vetted at a number of phases throughout this course of to make sure that no single buyer is identifiable by means of this knowledge – and that no single buyer’s knowledge skews the mixture inappropriately. When doubtful a few particular case, we excluded that buyer’s knowledge from the dataset.
Geography
Determine A1: Across the globe and up your road, it’s the Sophos X-Ops IR crew
The complete checklist of countries and different places represented within the 2023 report knowledge is as follows:
Australia
Italy
Singapore
Austria
Kuwait
South Africa
Belgium
Malaysia
Spain
Botswana
Mexico
Sweden
Canada
Netherlands
Switzerland
Colombia
Philippines
United Arab Emirates
Germany
Poland
United Kingdom
India
Saudi Arabia
United States of America
Industries
The complete checklist of industries represented within the 2023 knowledge for this report is as follows:
Agriculture
Meals
MSP/Internet hosting
Structure
Authorities
Non-profit
Communication
Healthcare
Pharmaceutical
Building
Hospitality
Actual property
Training
Data Know-how
Retail
Electronics
Authorized
Providers
Power
Logistics
Transportation
Leisure
Manufacturing
Utilities
Monetary
Mining
Methodology
The information on this report was captured over the course of particular person investigations undertaken by Sophos’ X-Ops Incident Response crew. For this preliminary report of 2024, we gathered case data on all investigations undertaken by the crew in 2023 and normalized it throughout 43 fields, inspecting every case to make sure that the information accessible was acceptable intimately and scope for mixture reporting as outlined by the main target of the proposed report.
When knowledge was unclear or unavailable, the authors labored with particular person IR case results in clear up questions or confusion. Incidents that might not be clarified sufficiently for the aim of the report, or about which we concluded that inclusion risked publicity or different potential hurt to the Sophos-client relationship, have been put aside. We then examined every remaining case’s timeline to realize additional readability on such issues as preliminary ingress, dwell time, exfiltration, and so forth. We retained 154 circumstances, and people are the inspiration of the report.





_dennizn_alamy_2.jpg?disable=upscale&width=1200&height=630&fit=crop&w=350&resize=350,250&ssl=1)














